 Twitter developer platform search field vulnerable to XSS Twitter developer platform search field vulnerable to XSS
Written by DPMonday, 6 September 2010*1st UPDATE* - Security researcher Mike Bailey (mckt) has produced a simple proof of concept which silently exploits this XSS. Basically, any Twitter user who clicks on the button will post a tweet reading
"@mckt_ just compromised my Twitter account with XSS. http://bit.ly/bvnkDB #twitterXSS".
Use it at your own risk:
http://skeptikal.org/exploits/twitter/twitter_xss.html
*2nd UPDATE* - As Stefan Tanase from Kaspersky Labs wrote in the news article "Τwitter XSS in the wild", cybercriminals - maybe of Brazilian origin - maliciously leveraged and exploited this Twitter XSS to steal user cookies and transfer them to two specific servers. According to bit.ly short link statistics, they have managed in a very short time to compromise more than 100.000 Twitter accounts by urging users to click on their link with a short tweet that read in portoguese "Pe Lanza da banda Restart sofre acidente tragico" (Pop band Restart suffering a tragic accident):

(Screenshot by Stefan Tanase of Kaspersky Labs)

(Screenshot by Stefan Tanase of Kaspersky Labs)
Twitter has confirmed the vulnerability is fixed now...
------------------------
This non-persistent Twitter XSS was submitted by "cbr" on July 29, 2010 and has not been corrected since then.
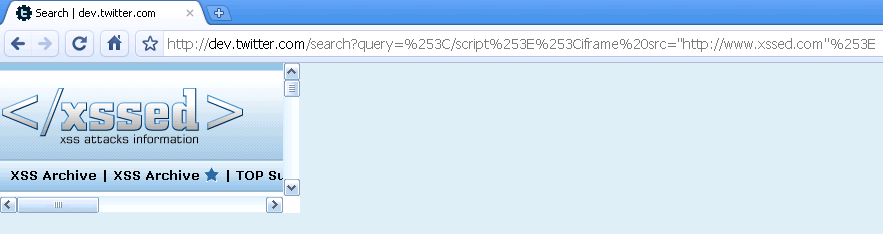
http://dev.twitter.com/search?query=%253C/script%253E%253Ciframe%20src="http://www.xssed.com"%253E%253C/iframe%253E [XSS Mirror]
During the summer period, another three possible XSS attacks on Twitter have been reported:
support.twitter.com persistent XSS vulnerability notified by d3v1l
twitter.com persistent XSS vulnerability notified by 0wn3d_5ys
and one by Billy (BK) Rios...
Important to mention that all were quickly fixed!
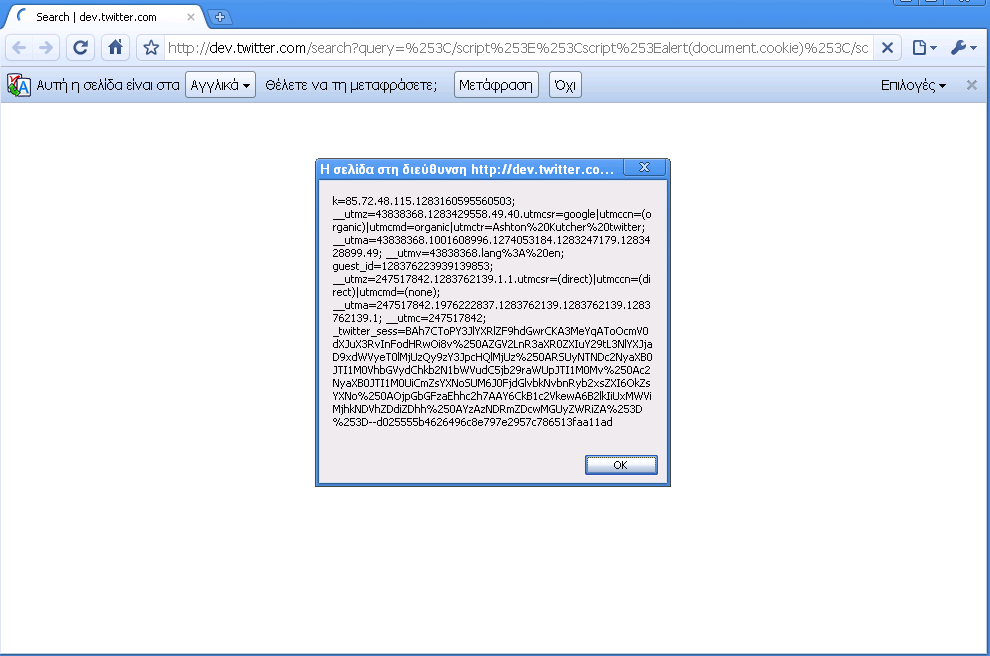
Screenshot #1:
Screenshot #2:
References:
"Just another persistent Twitter XSS" - DP - 19 Jul 2010
"Twitter XSS bug" - Billy (BK) Rios - 19 Jul 2010
"Persistent XSS vulnerability affecting Twitter promptly corrected" - DP - 27 Jun 2010
| 